This article is related to Wireshark application, and does not involve the implementation of kernel protocol stack.
Recently, I found an expert tip “TCP spurious retransmission” that I haven’t seen (or paid attention to) before, as shown in the following figure:
in the packet capture
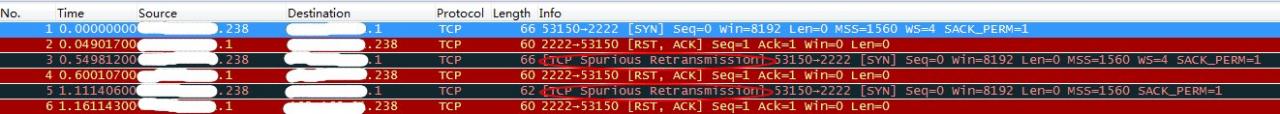
https://blog.packet-foo.com/2013/06/spurious-retransmissions/comment-page-1/ This is an additional prompt given by Wireshark to help users better understand the message process. The reason is that the sender resends a message segment that has received a response.
Back to this packet capture, the client initiates a connection request to the server. Because the corresponding port on the server is not open, it responds to the request with rst, and the rst responds to the initial sequence number. When the protocol stack tries to re initiate the connection again, the message will be marked as “spurious retransmission” by Wireshark.
Conclusion: pay attention to all knowledge.
Similar Posts:
- [original] TCP previous segment not captured
- SSL / TLS packet capture prompts ignored unknown record
- TCP segment of a reassembled PDU
- About Wireshark “the NPF driver isn’t running “Solutions
- [Solved] Cannot deserialize instance of `java.lang.String` out of START_OBJECT token
- [Solved] react native TypeError: Network request failed Unable to symbolicate stack trace: The stack is null
- XMLHttpRequest status=0 (All You Should Know)
- Run Wireshark or tshark as a Non-Root User
- [Solved] reactor.netty.http.client.PrematureCloseException: Connection prematurely closed BEFORE response
- Wireshark window size value and calculated window size