Make the browser no longer display the HTTP request alert in the HTTPS page
As HTTP over secure socket layer is an HTTP channel aiming at security, so HTTP requests are not allowed on the pages hosted by HTTPS. Once they appear, they will be prompted or an error will be reported
Mixed Content: The page at ‘ https://www.taobao.com/ ‘ was loaded over HTTPS, but requested an insecure image ‘ http://g.alicdn.com/s.gif ’. This content should also be served over HTTPS.
After the transformation of HTTPS, we can see the following alerts in many pages:
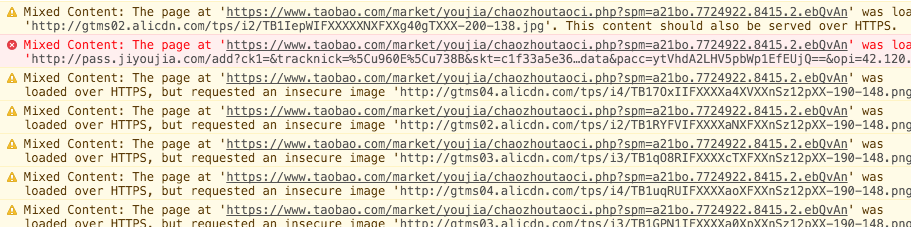
Many operators have no technical concept of HTTPS, so HTTP resources are unavoidable in the data filled in. The system is huge, and negligence and loopholes are inevitable.
CSP set upgrade insure requests
Fortunately, the W3C working group took into account the difficulty of upgrading HTTPS. In April 2015, it published a upgrade secure requests draft, which is to let the browser automatically upgrade requests.
In the response header of our server, add:
header("Content-Security-Policy: upgrade-insecure-requests");
Our page is HTTPS, and this page contains a large number of HTTP resources (pictures, iframes, etc.). Once the above response header is found on the page, it will be automatically replaced by an HTTPS request when loading HTTP resources. You can see a demo provided by Google
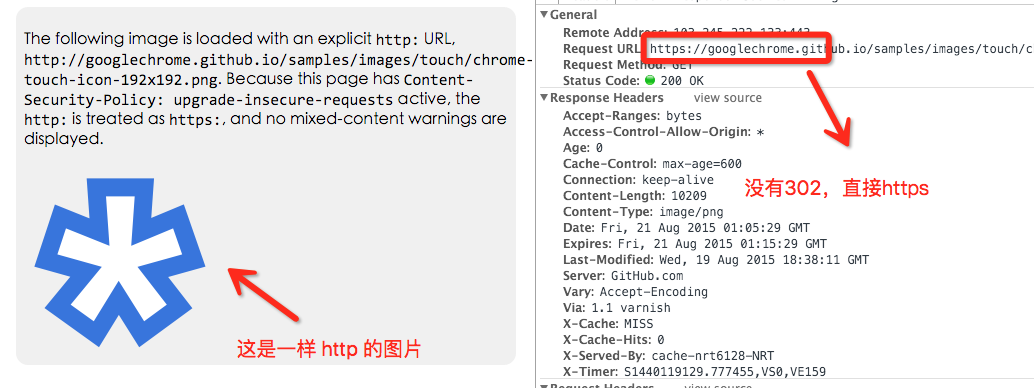
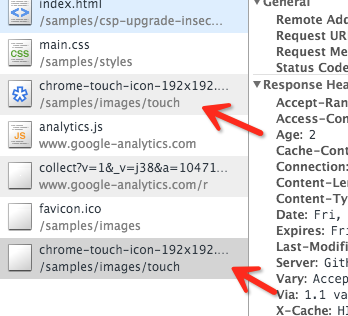
However, what is puzzling is that this resource has made two requests, which are supposed to be a bug in the browser implementation
Of course, if it is not convenient for us to operate on the server/nginx, we can also add the meta header to the page:
<meta http-equiv="Content-Security-Policy" content="upgrade-insecure-requests" /&>
At present, only chrome 43.0 supports this setting, but I believe that CSP will become the content that web front-end security pays great attention to and uses in the future. The upgrade insure requests draft will soon enter RFC mode.
From the example given by W3C working group, we can see that this setting will not deal with a link of foreign domain, so it can be used safely.
Buy me a cup of coffee 🙂
Similar Posts:
- This content should also be served over HTTPS
- Solution to the problem of missing URI path in chrome 85 + referer
- What does HTTP status code 304 mean
- When running Python script, an error is reported: a true sslcontext object is not available
- Resource interpreted as Stylesheet but transferred with MIME type text/html: css not work
- Solve the 400 error of nginx forwarding websocket
- Access to XMLHttpRequest at ‘http://localhost:9990/’ from origin ‘http://IP:Port’ has been blocked by CORS policy…more-private address space `local`
- Solution to cross origin read blocking (CORB) blocked cross origin response error
- Provisional headers are shown
- [Solved] Python request Error: requests.exceptions.ReadTimeout: HTTPSConnectionPool (xxxx)