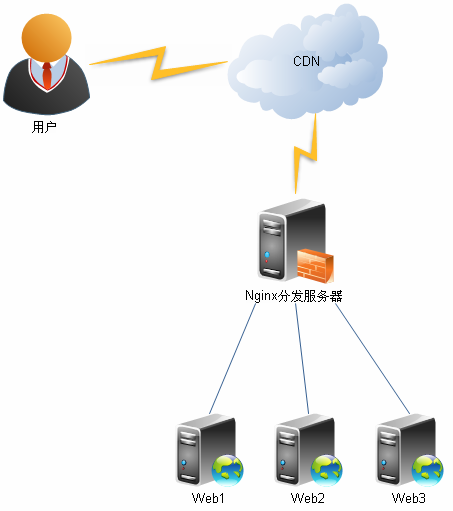
This is how the popular Java/PHP server gets the client IP:
Pseudo code:
1)ip = request.getHeader (“X-FORWARDED-FOR“)
can be forged, please refer to Appendix A
2) If the value is empty or the array length is 0 or equal to “unknown”, then:
ip = request.getHeader (“Proxy-Client-IP”)
3) If the value is empty or the array length is 0 or equal to “unknown”, then:
ip = request.getHeader (“WL-Proxy-Client-IP”)
4) If the value is empty or the array length is 0 or equal to “unknown”, then:
ip = request.getHeader (“HTTP_ CLIENT_ IP”)
forgeable
5) If the value is empty or the array length is 0 or equal to “unknown”, then:
ip = request.getRemoteAddr()
for anonymous proxy servers, the original IP can be hidden. Please refer to Appendix B for details
The reason for this trouble is that there are many kinds of network structures, such as nginx + resin, Apache + Weblogic, squid + nginx. Let’s talk about it one by one.
Zheng Yun
First of all, make it clear that nginx configuration is generally as follows:
location/{
proxy_ pass http://yourdomain.com;
proxy_ set_ header Host $host;
proxy_ set_ header X-Real-IP $remote_ addr;
proxy_ set_ header X-Forwarded-For $proxy_ add_ x_ forwarded_ for;
}
Pay attention to the red font, these configurations are related to the following IP.
———————————————————————————————
— the first level | x-forward-for: background –
This is a field developed by squid, not an RFC standard.
For short, XFF header , this item will be added only when it has passed the HTTP proxy or load balancing server. A detailed description of this item can be found in squid development documents.
XFF format is as follows:
X-Forwarded-For: client1, proxy1, proxy2
It can be seen that there can be multiple XFF header information, separated by commas in the middle. The first item is the real client IP, and the rest is the IP address of the agent or load balancing server.
— the first level | x-forward-for: scenario = client — CDN — nginx –
When a user’s request arrives at the nginx load balancing server after passing through the CDN, its XFF header information should be “client IP, CDN IP”.
In general, CDN service providers will shield the IP of CDN for their own security and only keep the client IP.
When the request header arrives at nginx:
by default, nginx does nothing with XFF headers
at this time, resin/Apache/Tomcat after nginx passes through request.getHeader The IP obtained by “x-forward-for” is still the original IP .
when nginx sets x-forward-for equal to $proxy_ add_ x_ forwarded_ For:
if the request from the CDN does not set the XFF header (this usually does not happen), the XFF header is the IP address of the CDN
compared with nginx, the client is the CDN
if XFF header is set in CDN, we set it again, and the value is $proxy_ add_ x_ forwarded_ For:
the XFF header is “client IP, nginx load balancing server IP” , so take the first value
this is a common scene!
To sum up, the XFF header is in the scene above, and resin passes the request.getHeader (“x-forward-for”) to get the IP string, do a split, the first element is the original IP.
So, can XFF headers be forged?
— the first level | x-forward-for: forgery –
can be forged.
XFF header is only a part of HTTP headers, which can be added, deleted and modified at will. As shown in Appendix A.
Many voting systems have this vulnerability, they simply take the IP address defined in the XFF header as the source address, so the third party can forge any IP vote.
———————————————————————————————
– the second and third level of proxy client IP/WL – proxy client IP : background –
Proxy client IP field and WL proxy client IP field only appear under the combination of Apache (Weblogic plug in enable) + Weblogic, in which “WL” is the abbreviation of Weblogic.
The access path is:
Client -&> Apache WebServer + Weblogic http plugin -&> Weblogic Instances
So these two levels are just compatible for us. I’m afraid you’ll suddenly change nginx + resin to Apache + Weblogic.
You can also ignore these two fields directly.
———————————————————————————————
HTTP client IP : background
HTTP_ CLIENT_ IP is the HTTP header sent by the proxy server.
Most of the time, the following is not included in nginx configuration:
proxy_ set_ header HTTP_ CLIENT_ IP $remote_ addr;
So this level can also be ignored.
Zheng Yun
———————————————————————————————
— the fifth level| request.getRemoteAddr (): background –
From request.getRemoteAddr () function definition:
Returns the Internet Protocol (IP) address of the client or last proxy that sent the request.
In fact, remote_ Addr is the IP when the client and the server “shake hands”, but if “anonymous proxy” is used, remote can be used_ Addr will display the IP of the proxy server, or the IP of the last proxy server. Please refer to Appendix B.
To sum up
the IP address obtained in Java/PHP may be forged or the IP address of proxy server.
ZHENG Yun: △
+ + + Appendix A XFF and nginx configured test cases + + +
Test environment: nginx + resin
intranet IP: 172.16.100.10
client IP: 123.123.123.123
test page: test.jsp
<%
out.println (“x-forwarded-for: ” + request.getHeader (“x-forwarded-for”));
out.println (“remote hosts: ” + request.getRemoteAddr ());
%&>
Nginx configuration 1
proxy_ set_ header X-Real-IP $remote_ addr;
proxy_ set_ header X-Forwarded-For $proxy_ add_ x_ forwarded_ for;
WGet test
wget -O aa –header=”X-Forwarded- For:192.168.0.1 ” ” http://test.com/test.jsp “
Page return result:
x-forwarded-for: 192.168.0.1, 123.123.123.123
remote hosts: 172.16.100.10
Curl test
curl -H “X-Forwarded- For:192.168.0.1 ” ” http://test.com/test.jsp “
x-forwarded-for: 192.168.0.1, 123.123.123.123
remote hosts: 172.16.100.10
nginx configuration 2
proxy_ set_ header X-Real-IP $remote_ addr;
proxy_ set_ header X-Forwarded-For $remote_ addr;
proxy_ set_ header X-Forwarded-For $proxy_ add_ x_ forwarded_ for;
WGet test:
WGet – O AA — header = “x-forward”- For:192.168.0.1 ” ” http://test.com/test.jsp “
page return result:
x-forward-for: 123.123.123
remote hosts: 172.16.100.10
curl test
curl – H” x-forward- For:192.168.0.1 ” ” http://test.com/test.jsp “
x-forwarded-for: 123.123.123.123
remote hosts: 172.16.100.10
test results:
1. Configuration
proxy_ set_ header X-Forwarded-For $proxy_ add_ x_ forwarded_ For;
a real IP x-forward-for is added, and the order is “after”.
2. Configuration
proxy_ set_ header X-Forwarded-For $remote_ Addr;
clears the incoming x-forward-for forged by the client,
ensures the usage request.getHeader The IP obtained by (“x-forward-for”) is the real IP,
or separated by “,” to intercept the last value of x-forward-for.
+ + + Appendix B test cases of Sogou browser in high speed mode
Access path:
“High speed” mode of Sogou browser (i.e. using proxy) – &> LVS — &> Apache
The values obtained are as follows:
x-forwarded- for:180.70.92.43 (real IP)
Proxy-Client-IP:null
WL-Proxy-Client-IP:null
getR emoteAddr:123.126.50.185 (Sogou proxy IP)
& amp; times; & amp; times; reference resources: & amp; times; & amp; times;
1, http://bbs.linuxtone.org/thread-9050-1-1.html
2, http://hi.baidu.com/thinkinginlamp/item/e2cf05263eb4d18e6e2cc3e6
3, http://bbs.chinaunix.net/thread-3659453-1-1.html
Similar Posts:
- Solve the 400 error of nginx forwarding websocket
- Fix Nginx 502 Error:upstream sent too big header while reading response header from upstream
- [Solved] docker nginx localhost connection refused connect() failed (111: Connection refused)while connecting to upstream
- Error during WebSocket handshake 403 [How to Solve]
- Nginx normal user startup configuration error: && springboot-swagger & Unable to infer base url
- [Solved] Nginx proxy Timeout: upstream timed out (110: Connection timed out)
- [Solved] nginx no resolver defined to resolve..
- Websocket failed: Error during WebSocket handshake: Unexpected response code: 400 [Solved]
- [Solved] Nginx reverse proxy 502 permission denied
- Solving the problem of nginx reverse proxy web service soap:address location problem